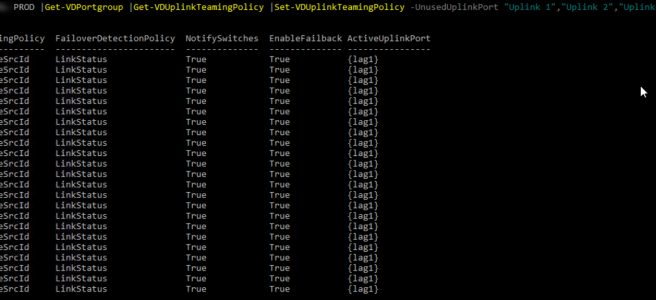
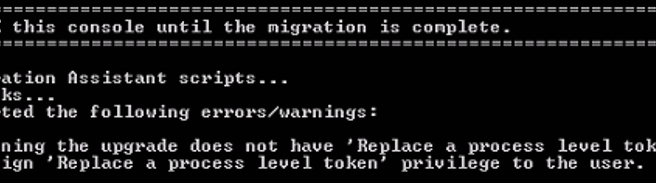
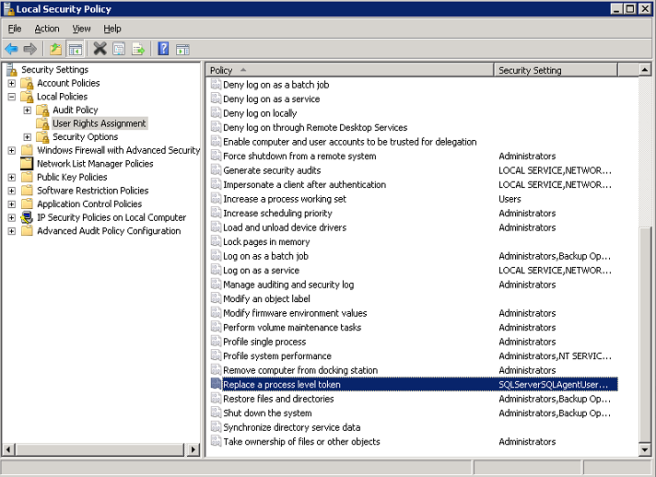
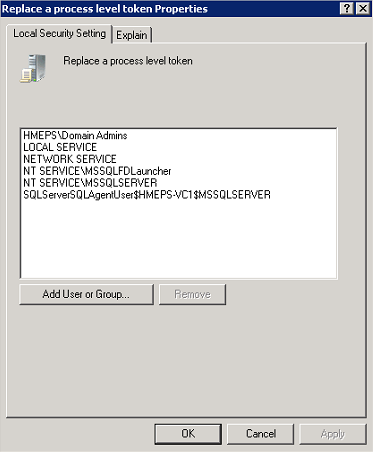
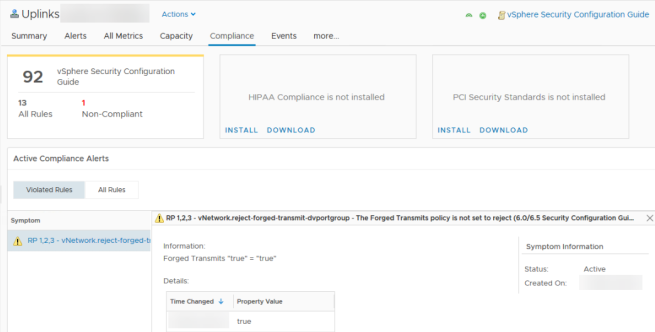
Recently I needed to configure LACP on a distributed switch that was already setup. With about 20 PortGroups (VLANs) already configured, the idea of clicking through each one to update the uplinks to the LAG from the standard uplinks sounded really boring.
I found this post by Ben Liebowitz on automating the creation of new port groups and stole the peices that I needed to just update the PortGroup active uplinks. So here it is.
Get-VDSwitch vDS-SwitchName |Get-VDPortgroup |Get-VDUplinkTeamingPolicy |Set-VDUplinkTeamingPolicy -UnusedUplinkPort "Uplink 1","Uplink 2","Uplink 3","Uplink 4" -ActiveUplinkPort lag1
Afterwards, I realised that it also updated the the active uplinks on the uplink port group. This change is not visible in the GUI and I’m not sure what the impact of this is but I figured that reverting it back was the best plan. So here is the command for that, if you were going to roll this out multiple times it would probably be a good idea to filter the above command based on the name of the uplink portgroup to avoid this change.
Get-VDSwitch vDS-SwitchName |Get-VDPortgroup vDS-SwitchName-DVUplinks |Get-VDUplinkTeamingPolicy |Set-VDUplinkTeamingPolicy -UnusedUplinkPort "Uplink 1","Uplink 2","Uplink 3","Uplin
k 4",lag1